GPON Dasan H660GM – leaking vlan in version 1.16-0003
Soon after releasing Dasan H660GM ONUs to our customers we got notified by script that a rogue DHCP exists in IPTV vlan. At a first glance I thought that one of our clients propably made a physical loop with an ethernet cable – from IPTV port to IT port. Such situation should be detected instantly by loop-detect mechanism offered by Dasan which works for us very well. Additionally – the MAC of the ‘rogue’ DHCP server was nearly identical as one of our H660GM which was deployed at customers location.
When I started to analyse the issue I noticed that this MAC is visible in IPTV vlan despite of that only one ethernet port was up on the ONU. It was ethernet port deisgnated for television service and the only MAC address I noticed there was a STB (set-top-box) device. I experienced such behaviour earlier regarding smart-switches, so let’s say – I wasn’t stunned at the beginning.
I was tempted finally and plugged my computer directly into the IPTV port of H660GM. I started tcpdump immediately.
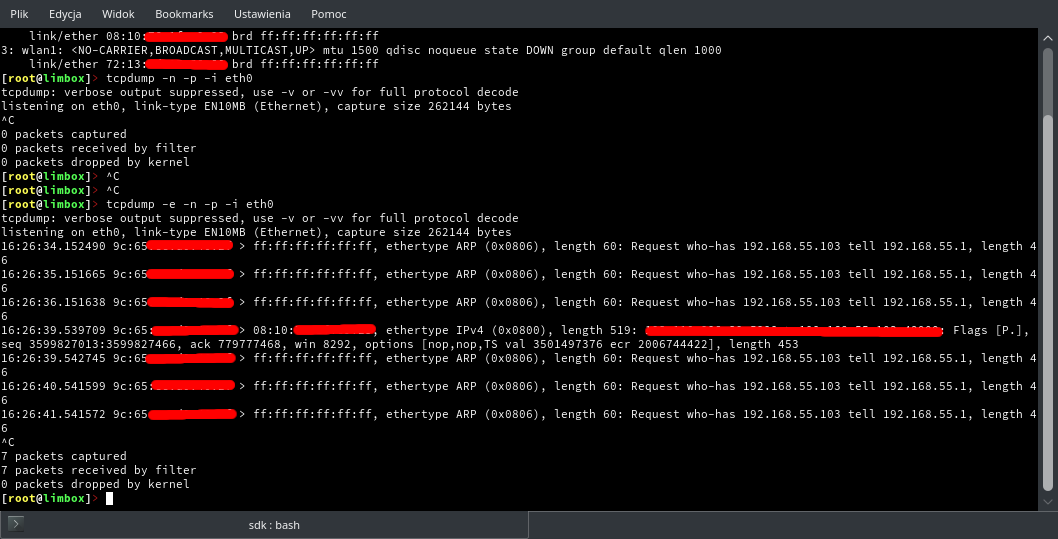
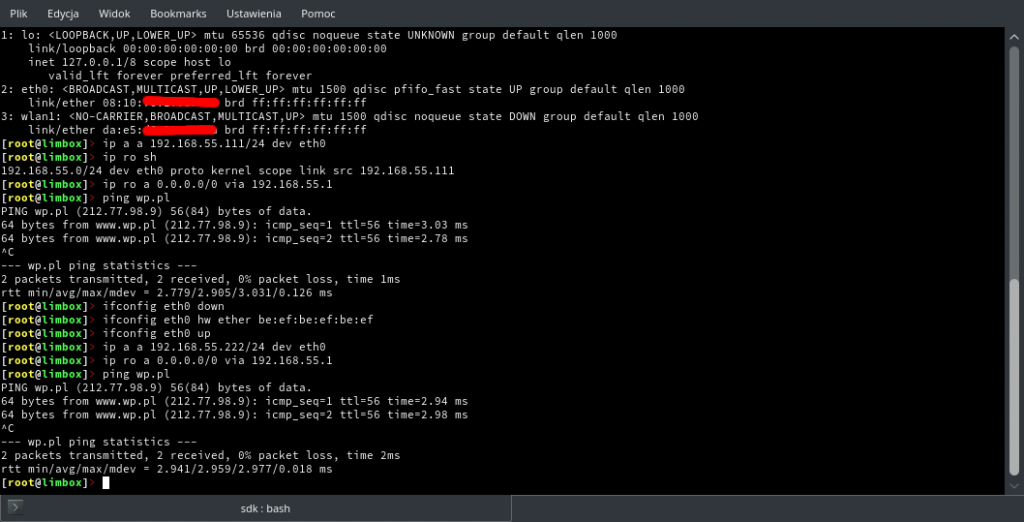
I added an address to the interface, static routing and well.. I had fully functional internet service access. What’s more interesting – DHCP packets from H660GM occured ocassionally. I tried to got an lease and it succeded once for every few hours. Just like something was filtering them.
Let’s see what NMAP scan results are.
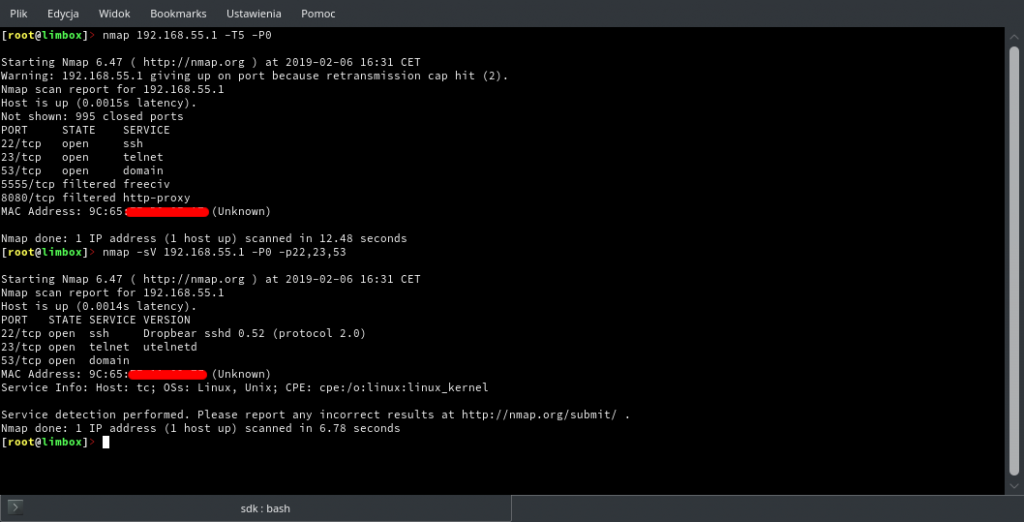
You can query its DNS port 53/UDP. Telnet is blocked permanently – it asks for a login and password, however you are unable to login.
When ISP does not change default credentials (which occurs fairly often) you can access H660GM shell easily. It works under MIPS architecture. Let’s see what we can find.
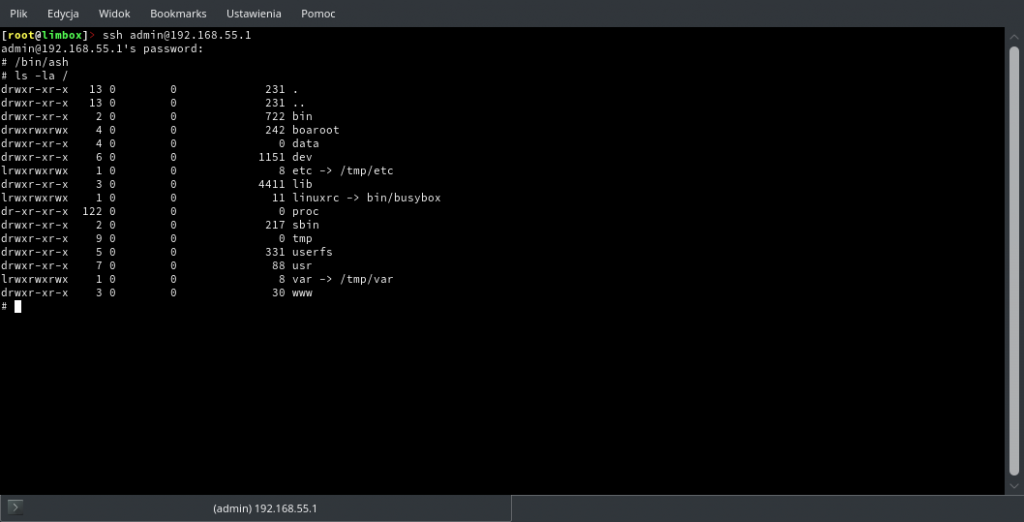
Seeking through filesystem we can find files which contents can be possibly dangerous for ISP if unauthorized access is achieved.
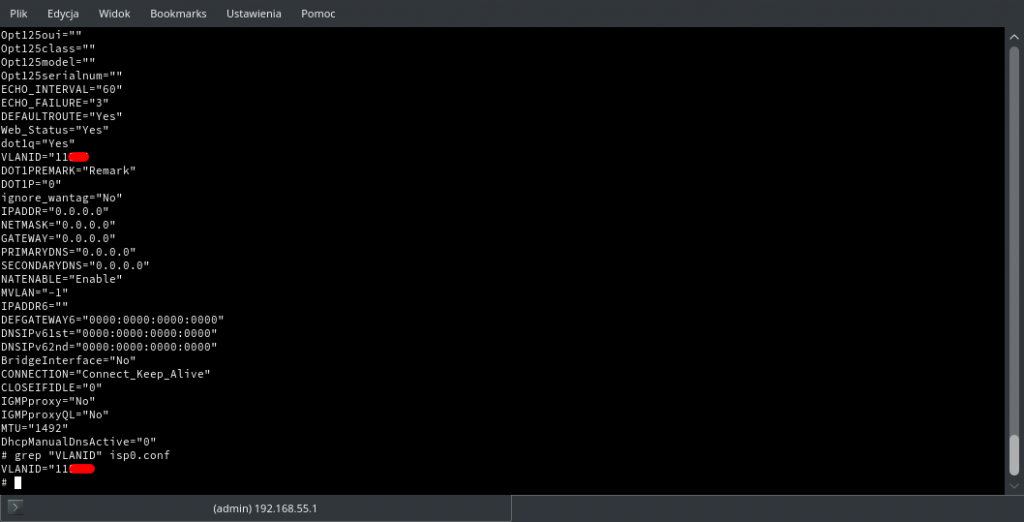
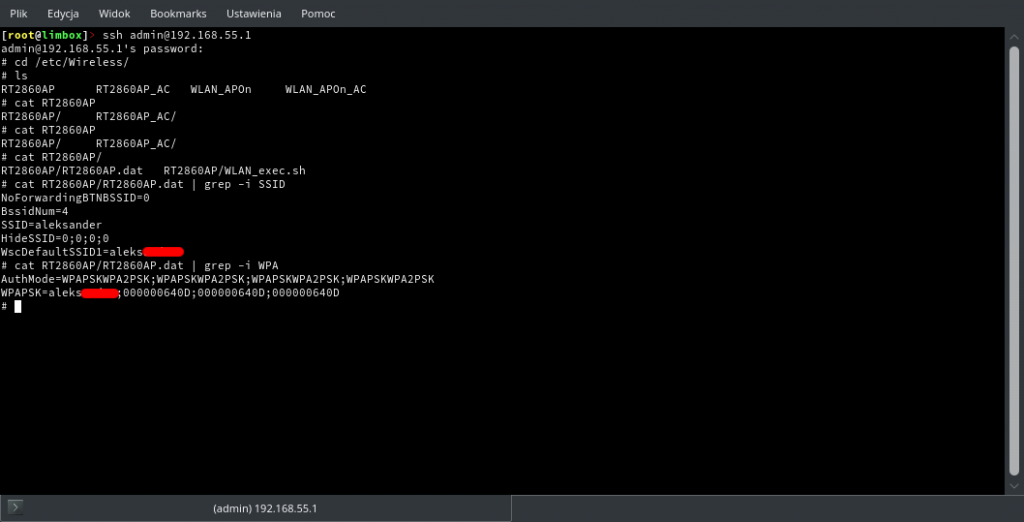
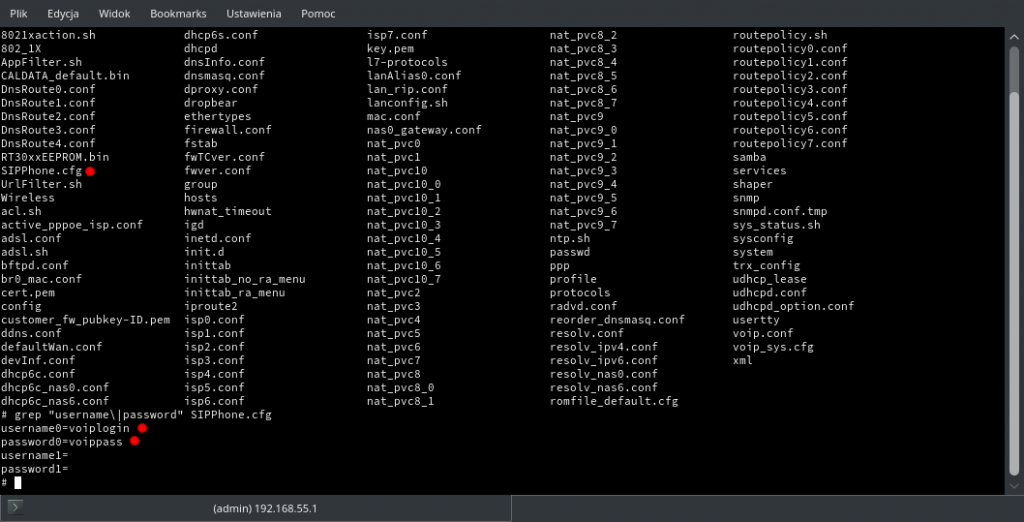
What’s interesting – while I have an address from 192.168.55.x pool, replies for arping to 192.168.55.1 are gatheres from every H660GM in that network segment. If you decide to add static ARP entry for all of them – you can access them without any problem. We are still assuming scenario when ISP does not change default credentials.
After reporting problem to the distributor we were gained access to RC1.16-0020 firmware which eliminates all of mentioned problems. Currently stable version is 1.16-0003 though… I recommend upgrading to release candidate version which works fine for us in production environment.
To sum up – if you use Dasan H660GM ONU devices and run 1.16-0003 firmware you can experience problems related to IPTV service. Propably customers’ STB are getting DHCP lease from other H660GM instead of authoritative DHCP server of yours. It’s really worth looking into!